Part 2 in our Information Security series provides insights on developing an Information Security strategy for higher education. In Part 1, Should We Worry About Information Security in Higher Education, we identified the security issues and threats in higher education and reviewed how a reactive or ad hoc approach to information security is not going to adequately address the issue.
What Should We Do About Information Security?
A large part of our journey in information security has been about moving from a disjointed set of activities to creating a program. The question of strategy gets to the heart of what it takes to move a program forward.
The Information Security strategy should be created and considered in such a way that it is built into an organization’s overall strategy. To provide the most value and relevancy to the institution, the information security strategy should strongly support the institution in its goals of educating students, conducting research and facilitating community outreach.
Moving from Reactive to Proactive: Gaining Control with a Strategy
Our approach to information security must evolve from short-term projects with small immediate goals into long-term programs with a mission, objectives, and strategy that improve the security posture of the organization. A mature information security program offers services that form a cohesive and coordinated effort to support the mission of the institution in a way that users understand and can implement.
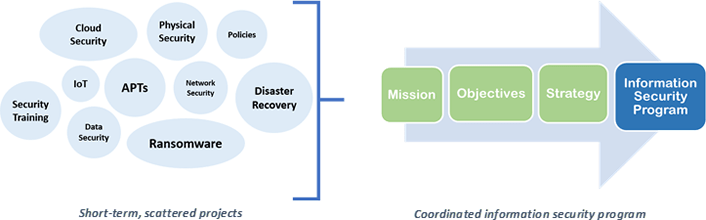
Moving from Disjointed Information Security Activities to a Coordinated Information Security Program
But how do you make the transition from a set of projects to a set of coordinated services that support the institution? Start by looking at your information security efforts as a program.
“An information security program is an organizational effort defined to meet an overarching purpose.
To make the transition to a comprehensive and proactive information security program, your approach needs to identify 3 key components:
- Mission – summary statement of the program’s purpose at the institution
- Objectives – establish a set of overarching program goals
- Strategy – a roadmap with guiding principles for moving from your current state to your desired state
Defining the Mission Statement for Information Security
In a simple sentence, a mission statement should describe the program’s purpose at the institution.
It is always useful to see how organizations have approached their mission statements. Here is how some colleges and universities described their information security mission statements:
- The mission of the University Information Security Office is to make information security programmatic and culturalon campus, enabling the University to succeed in its mission in teaching and research.
- The mission of the Cybersecurity Initiatives is to establish the university as a center of excellence in cyber security that encompasses research, education, workforce training and development, and promotes partnerships among the government, private and academic communities.
- Our Information Security mission is to support the University’s research and education mission by enabling the University community to mitigate risk to information assets.
- The mission of Information Security Services, within Information Technology Services (ITS), is to ensure the confidentiality, integrity, and availability of the University’s information technology resources and data by safeguarding them from compromise, misuse, loss or damage caused intentionally or unintentionally. This assurance will allow the University to continue its mission critical operations of education, research, service, and administration.
- The Information Security Team seeks to be a highly visible, responsive and effective team which enables the department, and wider collegiate-University, to deliver against its strategic aims reducing the risk of significant security incidents and data breaches.
Identifying Information Security Objectives
Overarching objectives are generally long-term aspirations or goals, aligned with the institution’s strategic plan, that require input from various sources. If you aren’t talking to campus leaders and stakeholders, this is your opportunity to spend time with them, learn their pain points regarding security (i.e. what keeps them up at night), and ask them how they measure success.
Then, formulate overall program objectives to help address your institutional risks and achieve institutional objectives. For example:
- Users will be armed with the awareness and knowledge to protect institutional data and meet compliance obligations.
- Users will effectively use program tools and services to protect institutional resources while carrying out position responsibilities.
- Information security leadership will be a trusted advisor/expert for institutional leadership.
- A robust set of security operations services exists to manage security obligations with respect to information resources.
Over time, overarching program objectives should lead to a coordinated set of efforts (e.g. projects and other activities) that are designed to achieve each objective. In fact, you should ideally be able to sort all your efforts under one or more of your overarching objectives. Doing this could help show where your efforts are serving the program objectives and where they may not be contributing good value in their current form. This can be an opportunity to reevaluate your options for achieving the program objectives, prioritize efforts, and communicate them in ways to help users understand how the individual project efforts are related to achieving program objectives. Be sure to include success metrics and assessments to check how well efforts are helping achieve those overarching objectives.
Developing a Clear Information Security Strategy
In “Demystifying Strategy: The What, Who, How and Why” by Michael D. Watkins in Harvard Business Review, a good strategy was defined as “a clear roadmap, consisting of a set of guiding principles or rules, that defines the actions people in the business should take (and not take) and the things they should prioritize (and not prioritize) to achieve desired goals.”
Creating a documented strategy can be challenging if you haven’t done it before. The key is to step back and apply intentionality to your direction. Think of your strategy as the sum of your guiding principles to optimize the security posture of the institution. Even though different higher education institutions have many program elements for information security in common, each institution’s information security strategy will be informed by its individual overarching objectives, risks, and culture.
There are several possible strategies that could be incorporated into your overall information security program strategy, and you can use some or all of these strategies.
Be Data Centric
If you choose to be “data centric”, you develop a strategy that revolves around data flows and securing them.
Empower Users
Settling on a strategy to empower users means that your focus will be on making sure users have the training, resources, and other tools they need to be security-minded and self-sufficient.
Be a Trusted Advisor
It may be important for your program success and campus culture that the information security office position itself be viewed as the trusted advisor for the campus, and the go-to source for consulting and advisement.
Foster Campus Partnerships
Part of becoming a trusted advisor requires fostering campus partnerships in which your program objectives are viewed as supportive and protective of academic and business efforts.
Achieve Unified Compliance
Finally, to combat compliance fatigue, many institutions are working toward unified compliance strategies as a way of combining and effectively addressing multiple compliance obligations.
These examples illustrate that strategies can account for the challenges that you are solving while attempting to reach your overarching objectives. Your strategy can also be an effective element of the value proposition that you intend to bring to the campus with your information security program. A good set of strategies should help your program turn the corner from reactive to proactive, create a cohesive set of efforts that are aligned with institutional objectives, and strike the right balance between security and other priorities at the campus level.
How Does the Chief Information Security Officer Contribute to Strategy?
As external threats grow and the complexity of managing disparate IT risks increases, the leadership role of the chief information security officer must become stronger and more strategic – and needs to move from a compliance monitor role to one that can create an organizational culture of shared ownership of security risks.
As such, the chief information security officer or CISO will play an important role in the development of the information security strategy by helping to:
- Lead the development of an information security program that leverages collaborations and campus-wide resources
- Facilitate information security governance, to advise senior leadership on security direction and resource investments
- Design appropriate policies to manage information security risk.
The complexity of achieving these objectives requires a sophisticated ability to work with other leaders to set the best balance between security strategies and other priorities at the campus level. Using the program elements of mission, objectives, and strategy can provide the institution with guiding principles and a guiding light to a successful information security program.
This blog post was based on an article titled “Crafting an Information Security Program Strategy” published in the Security Matters blog in EDUCAUSE Review on May 16, 2018 by Cathy Bates and Jon Young. Cathy and Jon are Senior Consultants with Vantage Technology Consulting Group working in the Strategic IT projects practice.


